Passwords: A secret for the whole world
Thursday, October 13, 2016
The Internet is full of recommendations about the need to use strong passwords and change them constantly. However, in practice, when a company establishes a policy to change passwords regularly, the result is usually sticky notes on monitors or, in a best-case scenario, under keyboards. And, of course, that’s not good. Using a password manager that generates strong passwords, stores them, and inserts them automatically when applications like browsers request them may seem like a good way to solve this problem. Indeed, this is very handy for users—and for hackers, too.
Denis Andzakovic, a security researcher at Security Assessment published the utility KeeFarce on GitHub. KeeFarce just has to be launched on the machine of an authenticated user of the password management utility KeePass, and the utility will decrypt all the password information and store it in a separate file (an attacker can retrieve the file immediately or get it later over a remote connection).
KeeFarce makes use of DLL injections. The malicious code uses KeePass's legitimate export routine so that the contents of the database that is currently in use (including all logins, passwords, notes and URLs) is saved as plain text into a CSV file.
https://xakep.ru/2015/11/05/keefarce
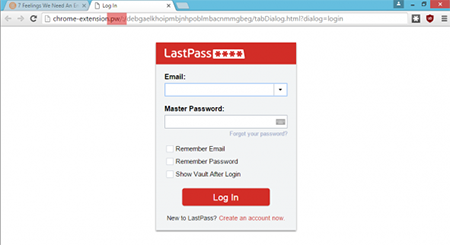
Security researcher Sean Cassidy discovered a phishing attack involving LastPass. He jokingly called it LostPass. First, criminals lure you to their site which displays a fake notification informing you that your session has expired and that you need to log in again.
Because the notification is fake, clicking Try Again directs you to a page that looks exactly like a LastPass authorisation web form. Even its URL will be similar to those displayed for service pages opened by browser extensions. Except for one small detail that I’ve highlighted in the screenshot. I’m sure that most users would not pay attention to such a minor thing.
Next you enter your username and password, and immediately they fall into the hands of the hackers. As a result, the latter gain full access to all of your sites and accounts. The attack is effective even if two-factor authentication is used. In this case the attacker will have to take one extra step. Find out more about LostPass here.
There are no invulnerable applications!
Many users often work with several computers and launch password managers from removable media. Because these applications typically require external libraries, the ability to download libraries without proper authorisation can be exploited (if a corresponding vulnerability exists) to make the password manager distribute dangerous malware.
https://xakep.ru/2014/09/08/password-manager-pentest
Only one out of five password managers tested were able to withstand all attacks and keep information stored safe. Yet some users who left comments emphasised the fact that some features weren't used in the attacks. And time proved them right.
In February 2016, security researcher Florian Bogner discovered a vulnerability in password manager KeePass versions 2.x: he connected to KeePass update servers via HTTP so that a man-in-the-middle attack could be mounted to replace a legitimate update with a malicious file. Furthermore, the password manager doesn't verify downloaded update packages, which makes the attackers' job even easier.
The Anti-virus Times recommends
- Indeed, password managers are easy to use and much more secure than opting for the same password to access all sites or choosing a weak password that is simple to remember (and to crack, too), but, regardless of what measures you introduce, common sense on the part of users remains the most essential security component.
- Most of the problems with the password managers we've described above occur when a system is infected with malware. Therefore, if you care about your passwords and have entrusted them to your computer, remember: an anti-virus is a must-have!
- However, there is one password you will need to remember and change regularly—the one you use to access the manager. Important! Password managers do not store their master passwords on a hard drive and users have to enter them manually whenever they use the application. Attackers use key loggers to intercept those passwords. They can also record cursor movement and take screenshots (if a virtual keyboard is in use).
- Once you’ve finished working with a password manager, make sure you close the application.
- Important sites should not allow you to log in automatically. That should only be possible on sites that users visit several times per day and those that do not contain critically important information.
- When selecting a password manager, pay attention to the location where your passwords will be stored (local drive or cloud). If passwords are stored locally, you’ll be able to use the manager even if Internet access is unavailable. There is also no risk of the remote storage becoming compromised. On the other hand, if you have several devices, you’ll need to enter passwords yourself on the ones that don’t have a password manager, or use a cloud service.
And, to close: a few words about how password manager developers regard user security. We’re talking about the KeePass vulnerability mentioned above.
The researcher notified KeePass’s developers about the problem in February 2016. However, the company’s head, Dominik Reichl, replied directly to the researcher and reported that the vulnerability won't be closed.
"This vulnerability won't be closed. The indirect costs involved with switching to HTTPS (e.g., lost advertising revenue) make closing it unviable”, wrote Reichl.


![Shared 16 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
08:19:51 2018-07-01
Helen
13:53:17 2016-10-14