When a presentation does more harm than good
Monday, November 7, 2016
Probably everyone already knows that criminals send malware as attached executables. And most of us have heard the recommendation to disable the transfer of executable files in emails; we aren't surprised by this because office workers don't need to install software themselves.
But presentations are a whole different story. Office workers, as well as others, create and view presentations, which nowadays can include much more than just text and images!
OLE (Object Linking and Embedding) is a proprietary technology developed by Microsoft that allows objects to be embedded in documents and other objects. The technology was later incorporated into ActiveX.
With OLE, a program can transfer a portion of the work undertaken by one application to another application (e.g., data conversions) and return the results. For example, desktop publishing software can use OLE to transfer a text to a text processor or send a picture to an image editor.
OLE can facilitate data exchange between various programs via the OLE Object interface or using Clipboard.
The vulnerability CVE-2014-4114 was discovered in 2014. Attackers use it to embed malicious code into PowerPoint documents and bypass anti-virus protection.
In June through October 2014 this vulnerability was exploited for espionage in the Sandworm project, but today ordinary cybercriminals know about it and use it in mass phishing attacks, sending out emails with .PPS files attached.
The vulnerability CVE-2014-4114 affects Windows Vista SP2 and later, up to Windows 8.1, as well as Windows Server 2008/2012 and Windows RT Gold and 8.1.
Essentially, this vulnerability lets attackers copy an INF file contained within an OLE object from a shared folder onto a target machine. A document crafted by attackers can contain a link to an executable file that can be downloaded and launched.
An attacker who successfully exploits this vulnerability could run arbitrary code in the context of the current user. If the current user is logged on with administrative privileges, an attacker could install programs; view, change, or delete data; or create new accounts with full user rights.
This attack is particularly dangerous because all the malware components that perform the attackers' tasks are activated within one application. Focused on checking files that are launched from a hard drive, an anti-virus may fail to respond to the threat because no malicious component will be written onto the disk.
#Vulnerability #security #security_updates #Dr.Web_settingsThe Anti-virus Times recommends
- Timely updates will substantially improve your system's security. To close the vulnerability, just install the corresponding security update. The vulnerability was discovered in 2014, but even now, the number of computers lacking the released security patch is large enough to attract criminals' attention.
- Malicious code can only be executed if a duped user allows it. Do not open all your email indiscriminately even if malicious attachments appear to be absent.
- An anti-spam will help you avoid attacks via email—all malicious messages will be filtered out before they are received by your mail client. You will never encounter a threat!
- The HTTP monitor Dr.Web SpIDer Gate and Dr.Web SpIDer Mail scan traffic before it is processed by applications and detect malicious code prior to its execution.
- The Parental/Office Control black list list will make sure no content is downloaded from dubious sources. You can configure restrictions as you see fit. For example, you can choose to disable access only to specific sites.
To access Parental/Office Control black list settings, click on the icon  in the system tray, and enable access to the settings by clicking on the padlock icon
in the system tray, and enable access to the settings by clicking on the padlock icon  (the icon will change to
(the icon will change to  ). Then click on the gear icon
). Then click on the gear icon  , go to the Tools menu, and select Parental (Office) Control.
, go to the Tools menu, and select Parental (Office) Control.
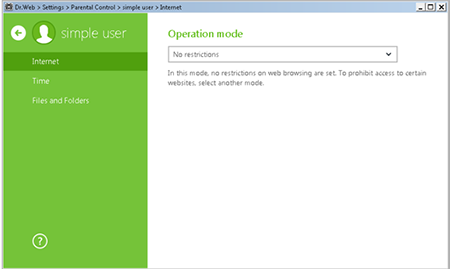
If no access restrictions have been set for certain sites, No restrictions will be displayed in the Internet section.
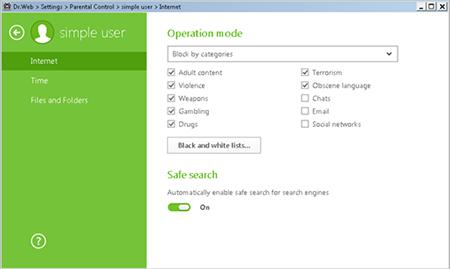
Select Block by categories to restrict access to sites that fall within the predefined groups. If you select this option, you will be able to define thematic groups (adult content, violence, weapons, etc.) for sites you want blocked. Select the groups you need.
You can also block access to all websites except those added onto the white list. To do this, select Block all except websites from the white list.
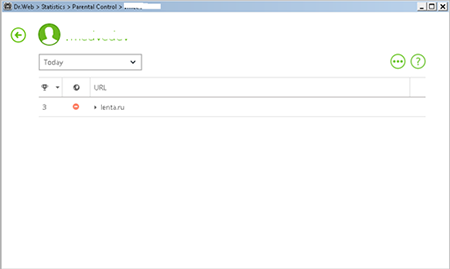
To view statistics about user requests to various sites, in the Agent menu, click  and select a username.
and select a username.


![Shared 17 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
05:15:51 2018-08-23
vasvet
07:08:56 2018-07-21