Search, find, and get infected
Monday, December 5, 2016
Some people think the Internet is just one big cesspool. Of course, those are the skeptics, but there’s no smoke without fire. The Internet is full of useful information, but no one can deny the fact that it has become a place where criminals feel right at home.
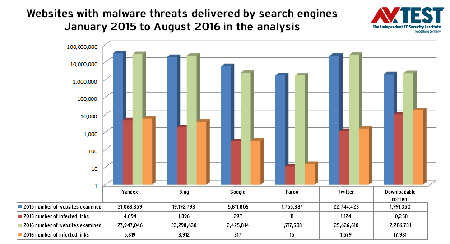
Search engines like Google provide access to one billion resources worldwide and process four billion to six billion user requests daily. However, how many malicious links are hidden in the search results? In 2015 and 2016, AV-Test, an independent German IT security institute, examined 80 million websites and more than 315 million tweets on Twitter in 2015, and another 200 million tweets in 2016. The resulting diagram, shown below, illustrates the increase in the number of links with malicious content that was detected for various search engines.
You can see that malicious Internet content is increasing from year to year:
- 2013: 40 million websites scanned; 5,060 infected pages detected.
- 2015: 80 million websites scanned; 18,280 infected pages detected—a threefold increase in two years!
- 2016 (up to August): 81 million websites scanned; 29,632 infected pages detected—a 60% increase in just the first half of the year!
According to the analysis, in more than 60% of the cases, the attack was carried out by loading a file, and only 40% of the attacks exploited vulnerabilities and implemented exploits in Java, Flash, and other components. The most common file formats used by malware are as follows:
- EXE – executable files;
- ZIP – compressed archives;
- RAR – compressed archives;
- SWF – Adobe Flash media files;
- MSI – Microsoft Windows Installer files.
The Anti-virus Times recommends
- Filtering incoming executable files and prohibiting them from being launched allow the number of vulnerabilities created by careless users to be significantly reduced.
User carelessness can occur at any level, regardless of position and responsibilities:
Russian Federation Council Member Ludmila Bokova, Chairperson of the Council of Federation Committee on the Development of the Information Society, fell into a trap set by a 24-year-old phisher.
After hacking into her email account, the cybercriminal sent emails to Bokova’s friends asking them to help raise funds for medical treatment for her sick niece.
https://life.ru/t/телеком/922624/sienator_liudmila_bokova_otviechaiushchaia_za_it_poimala_khakiera
So, for the hundredth time we’ll repeat: restricting user access rights and using an effective anti-virus are the norm!
- Despite the growing number of news stories about cybercriminals being brought to justice, most of them are not in jail. Law enforcement authorities aren’t the only ones to blame for that. Do you know how many people have submitted statements to the police about hackings or infections? How many people have addressed their local elected officials with a relevant initiative or a request to change the law? As you know, might makes right, and the sleeping fox catches no chickens!
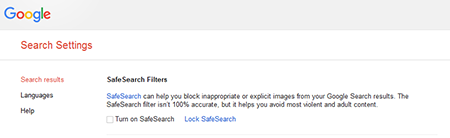
And, in conclusion, we’ll reveal to you a little-known fact. You probably know that Dr.Web anti-virus products that filter Internet access use lists of resources that have been deemed to be malicious. But very few people know that those anti-virus products also utilize search results. When you do a search on Google, Yandex, Bing, Yahoo! and Rambler, the results displayed are only for websites that are safe (from the point of view of the search engines and Dr. Web). When enabled, the "Safe search" option makes this possible—unsafe content is filtered out by the search engines!


![Shared 16 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
12:33:16 2018-07-15