Wanna Cry. Close the ports
Thursday, June 15, 2017
The encryption ransomware WannaCry gained extensive publicity and left many users without their data. But WannaCry can only penetrate a machine if the following conditions are met:
- Security updates haven't been installed. This happens if automatic updates are disabled in a system, a user has rejected the option to install updates, or the operating system is no longer supported by its developer.
- The ports targeted by criminals are open. Specifically, port 445.
- SMB v1 is enabled.
If at least one of these conditions is not met, the ransomware won't be able to infect the machine.
Let's see how ports can be closed.
As a rule, there is no way to tell which ports aren’t needed. Let's consider just a few of those that aren't normally used on PCs unless they are connected to a local network.
| Port | Description |
|---|---|
| 135 | MSRPC (Microsoft RPC). The port is utilised by network applications from Microsoft. If your mail client doesn't connect to an Exchange server, it is quite possible that you don't need it. |
| 137 | NETBIOS-NS (NetBIOS Name Service) |
| 138 | NETBIOS-DGM (NetBIOS Datagram Service) |
| 139 | NETBIOS-SSN (NetBIOS Session Service) |
| 445 | MICROSOFT-DS — used in Microsoft Windows 2000 and later to provide direct access over TCP/IP without resorting to NetBIOS (e.g., by Active Directory) |
There are several ways to close a port you don't need. For example, you can execute the following commands with administrative privileges in the command prompt:
netsh advfirewall firewall add rule dir=in action=block protocol=tcp localport=135 name=″Block_TCP-135″
netsh advfirewall firewall add rule dir=in action=block protocol=tcp localport=137 name=″Block_TCP-137″
netsh advfirewall firewall add rule dir=in action=block protocol=tcp localport=138 name=″Block_TCP-138″
netsh advfirewall firewall add rule dir=in action=block protocol=tcp localport=139 name=″Block_TCP-139″
netsh advfirewall firewall add rule dir=in action=block protocol=tcp localport=5000 name=″Block_TCP-445″They work for Windows 10. Under Windows 7 you have to add the registry entry:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 -Force
Performing the above steps requires some experience.
But Dr.Web users have an easier way to do this.
#Dr.Web #Trojan.Encoder #firewall #ransom #extortion #Data_Loss_Prevention #encryption_ransomware #ransomware #TrojanThe Anti-virus Times recommends
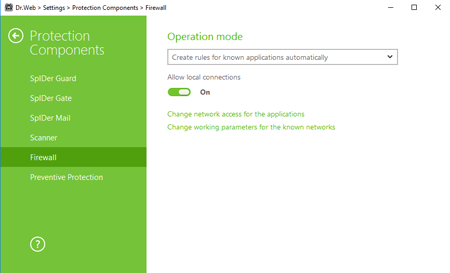
The Dr.Web firewall protects a computer from unauthorised access and prevents sensitive data from being leaked over the network. The component allows connections and data transmission to be controlled and suspicious connections on the package and application layers to be blocked. In particular, it allows unused ports to be blocked.
To configure the firewall, click on the icon ![]() in the system tray; click on the padlock icon
in the system tray; click on the padlock icon ![]() to make the settings accessible (the icon will now look like
to make the settings accessible (the icon will now look like ![]() ). Then click on the gear icon
). Then click on the gear icon ![]() . In the settings window select Protection Components → Firewall.
. In the settings window select Protection Components → Firewall.
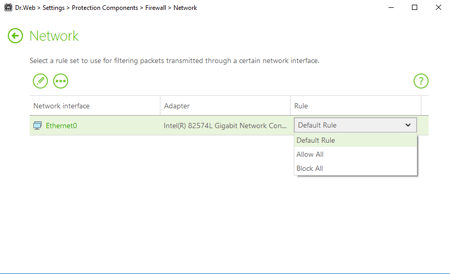
Select Change working parameters for the known networks and the network interface in use. Active interfaces will be displayed in the table automatically.
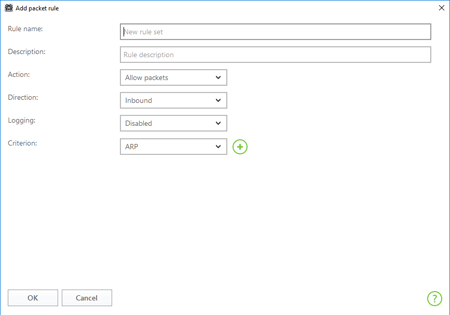
To create a set of rules for a new program, click Create.
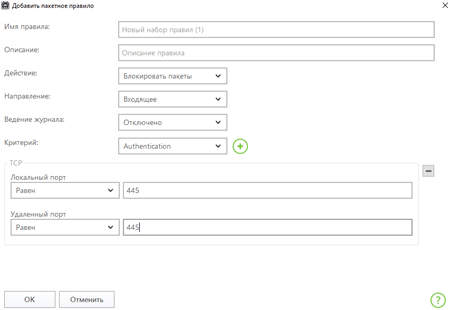
In the Criterion list, select TCP and specify the port number.
Press OK.
So, as you can see, Dr.Web anti-virus solutions provide reliable protection from the latest threats, including WannaCry.


![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
04:07:47 2018-07-22
vasvet
11:39:05 2018-07-21