Infected from a distance
Friday, July 29, 2016
Is there life after an infection (for example, after your server has been compromised by encryption malware)? The server’s been restored, and the user who unknowingly facilitated the infection was reprimanded... Can you just move on?
Modern-day malware is often a multithread complex designed to pump money out of you and your computer. If you’ve paid a ransom to restore access to your server’s data, it is far from certain that your troubles are over. It is possible that when the intruders stole the passwords and logins of your services, they turned around and resold them on the black market for use in a targeted attack.
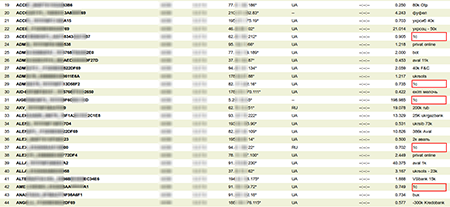
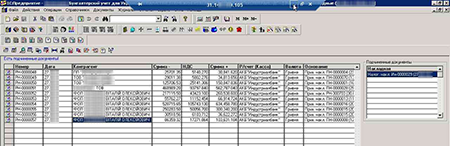
Screenshots taken from infected computers at the moment 1S, an accounting program widely used in Russia and CIS countries, was accessed remotely via RDP.
Some attackers are so extreme in their activity that, in addition to 1S data encryption, they don’t miss the opportunity to install additional software on a server to, for example, automatically search for vulnerabilities in the engines of different sites (e.g., WordPress).
www.cys-centrum.com/ru/news/attackers_hack_accounting_servers_with_1c
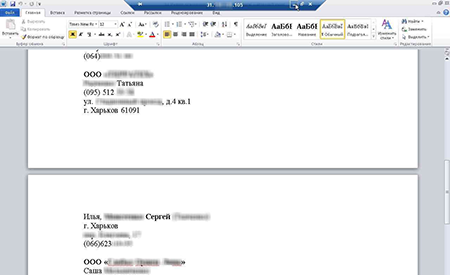
Furthermore, once they’ve received the ransom for the data they’ve stolen from you, criminals make no guarantees that they won’t use the data to blackmail you or your colleagues—or let whoever buys your data do that.
The Anti-virus Times recommends
Remote access to online banking is one of the traditional paths of attack being used successfully by hackers. To prevent possible remote access, follow these recommendations:
- Disable remote access to your server. And, if you need to use remote access—change the standard network port number (3389/tcp) to a different one.
- Use strong passwords and change them often.
- Block the sources/accounts from which brute force attacks are performed—after a certain number (3-5) of incorrect login/password combinations have been entered.
- Do not use standard user accounts.
- Allow remote access only from specific addresses/subnets.
- In case of any attack, we recommend that you change all of your passwords and logins. It is far from certain that the intruders involved have only compromised one computer.
- Don’t forget that regular data backups are a necessity, but not a remedy. If a malicious file has existed on your server for a long time, it’s quite possible that all your copies are infected.
- Regularly check whether it’s possible to restore your data from backups.
- Update your anti-virus regularly. Don’t forget that the anti-virus must use the update system under the control of self-protection—only in this case can we guarantee the delivery of updates to an infected server.
- Use Dr.Web Office Control to restrict a user’s access to data they don’t need.
- Monitor network traffic using Dr.Web Firewall—configure it with a list of programs that can connect to the Internet.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
12:45:56 2018-07-15