Fired and angry
Friday, December 9, 2016
It's no secret that employees are often dissatisfied with their employers. And, if before they quit, their discontent is usually expressed via instant messengers and water cooler conversations, once they’re gone for good, things may change dramatically. And it doesn't end with negative company reviews on the Internet.
- A company discovered that one of its employees is reasonably well versed in web design and programming, and asked him to develop a corporate website. A few months later the employee was reprimanded for regularly shirking his duties, and the company's president told him that management was going to fire him. That same day, the resentful employee remotely logged on to the corporate network, erased some data, and changed the text and pictures on the website. When police arrested the culprit, he explained that he got angry because the employer fired him.
- A system administrator, who worked for a prosperous company in the military industry, got angry with his bosses. He believed that they undervalued him while he was working hard to set up and maintain the entire corporate network. So the employee moved the industry workflow software used by the company to one server. After that he coerced his colleague into giving him the only software backup. After management fired the system administrator for his threatening and inappropriate attitude toward his colleagues, the logic bomb exploded. The angry employee erased all the data on the server, causing the company damages in the amount of $10 million, which led to the dismissal of 80 employees.
- An application developer was downsized out of his job at an IT company. In retaliation, the former employee attacked the firm's network just before the Christmas holidays. Three weeks later, after his dismissal, he remotely logged on to the corporate network using his former colleague's account, modified data on the company's web server, changed the text and published pornographic images on the company’s website. After that, the disgruntled developer sent emails to all the company's clients proposing that they open the corporate website and verify for themselves that it had been compromised. Each message contained a client login and password to access the site. An investigation was started, but it failed to identity the offender. Six weeks later the perpetrator once again remotely accessed the network and launched a script that altered all the passwords on the network and modified 4,000 entries in the price database. This time he was identified and arrested. He was sentenced to five months in prison and two years’ probation. The punishment also included a $48,600 fine, which he had to pay to his former employer.
- A municipal servant wasn't appointed a financial officer. Another employee took the position. To get revenge, the infuriated bureaucrat deleted all the files on his computer and the computers of his colleagues the day before the new financial officer was due to assume the position. The investigation that followed proved that the employee was guilty, but because many of the files were restored, the local government agreed to refrain from starting criminal proceedings and allowed the perpetrator to quit.
In such cases, the perpetrators don’t necessarily have a criminal background—only in 30% of the investigated cases had staff members been previously arrested at least once. But the fact that such people tend to be associated with information technologies is a certainty. To a large extent, this happens because using information technologies to exact revenge appears to be easier and safer than attempting to inflict material damage or resort to violence. People of this kind also consider themselves to be solid professionals, which in their eyes makes them immune to punishment.
Research conducted by CERT (computer emergency response team) shows that virtually all corporate saboteurs are somehow related to information technologies.
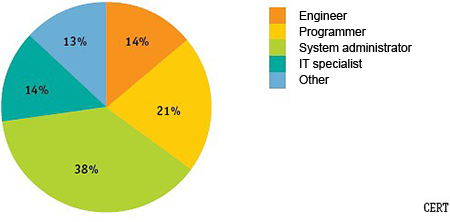
Tech savvy people account for 86% of the incidents.
Among them, 38% are system administrators, 21% are programmers, 14% are engineers, and 14% are IT professionals. As for saboteurs who don’t work in technical departments, 10% of them are editors, sales specialists, auditors, etc., and 3% are service people, specifically those who communicate with clients.
The Anti-virus Times recommends
Unfortunately, company negligence is behind many acts of vandalism: perpetrators had full access to corporate IT environments after they left their jobs. Eighty-nine percent of employees retained access to at least one corporate service after their dismissal. Naturally, far from all of them will become perpetrators.
Indeed, it can take a great deal of time to convey all the information about system administration to a new joiner, and often former employees provide assistance to their former employers. But should they be granted full access or rather receive the required permissions only when necessary?
- Change access passwords as soon as employees quit.
- Suspend or remove all accounts of former employees after they vacate their position or after the transitional period is over and their mail is redirected to other employee inboxes.
- If you are considering giving an employee the boot and their loyalty is somewhat questionable, restrict their access to your corporate IT environment beforehand.
Taking extra precautions may prove to be very useful!


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
05:25:42 2018-08-23
vasvet
08:49:28 2018-07-01