Everything’s protected!
Thursday, April 27, 2017
Cybercriminals use any means possible to break into a victim's computer—for example, scripts.
A script is a type of computer program. Like traditional programs, scripts perform a sequence of actions and can be quite complex. But, unlike programs, scripts, once written, are not transferred into executable code (they don’t go through the compilation stage). They are run with the help of an external program (interpreter) and will not work without it.
For example, very often webpages use scripts written in JavaScript. Using scripts is particularly helpful when it comes to making pages easy to view, without having to create separate pages for different browsers and even different screen resolutions.
The advantage of scripts is that they can be used across different platforms: the same script can be run on a variety of devices and operating systems. And virus writers have duly taken note of that.
Let's start with the fact that a virus is a rather complex object, and it usually consists of multiple modules. One of them is an exploit. Its main goal is to exploit an already known vulnerability for the purpose of executing arbitrary code (for example).
If we scroll down this list of vulnerabilities, we'll see that many of them include JS.
A browser, like any other complete application, can access the file system (normal access that makes it possible to write, read, and create non-system files) using the API of the operating system (for example, WinAPI for Windows). Inside it looks like a system call—a program transfers control to the kernel level, having previously been informed that some file needs to be opened/created/written.
And, by the way, after that, the browser will probably crash. But that no longer matters—the code will be implemented and executed. Of course, this is a trivial thing, and there are 100,500 different variants nobody will tell you about, but the idea is clear.
Does that scare you? In reality, malicious files implemented with the help of JavaScript are used for more than simple goals—e.g., downloading malicious files. And they don’t cause any problems for a browser. Just opening any Doctor Web monthly review will convince you that JavaScript is popular among virus writers:
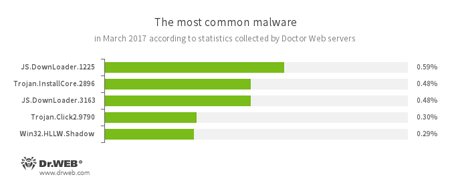
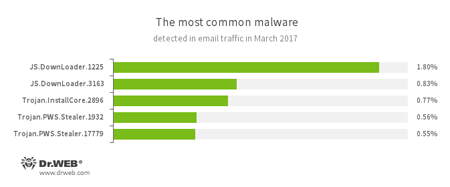
JS.DownLoader — a family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer.
Of course, anti-virus developers could not help but notice this threat, and in 2011 a new technology was added to Dr.Web.
ScriptHeuristic prevents any malicious browser scripts and PDF documents from being executed without disabling the functionality of legitimate scripts. It protects against infection by unknown viruses that try to access systems via web browsers. It works independently of the Dr.Web virus databases, in any web browser.
The convenience of scripting languages is that they automate day-to-day actions, without requiring the installation of development tools. To use a scripting language, it is enough to have the simplest text editor installed and the corresponding operating system component responsible for executing the corresponding scripts. The fact is that JavaScript is not the only scripting language you can come across on your computer. For all its convenience, this language is optimised to be used in browsers. In this regard, Microsoft has developed an equivalent for JavaScript—JScript. JScript is executed with the help of Windows Scripting Host (WSH).
Windows Script Host (WSH; formerly named Windows Scripting Host, renamed for the second release)—a Microsoft Windows component designed to run scripts in JScript and VBScript, as well as in other additionally installed languages (for example, Perl).
An example of JScript:
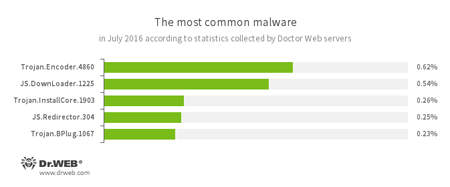
Trojan.Encoder.4860
A ransomware Trojan also known as JS.Crypt. Written completely in JScript, this Trojan is distributed under the name “RAA virus”, and all locked files are appended with the extension *.locked.
Another scripting language is PowerShell.
Windows PowerShell is a task automation and configuration management framework from Microsoft, consisting of a command-line shell and associated scripting language.
PowerShell also provides a hosting API with which the PowerShell runtime can be embedded inside other applications. These applications can then use PowerShell functionality to implement certain operations, including those exposed via the graphical interface.
Windows PowerShell 2.0 was released as an integral part of Windows 7, Windows 8, Windows Server 2008 R2, and Windows Server 2012 R2. Besides, the second version is available for other systems such as Windows XP SP3, Windows Server 2003 SP2, Windows Vista SP1, Windows Vista SP2, Windows Server 2008 and Windows Server 2012.
Windows PowerShell was built on the Microsoft .NET Framework and integrated into it.
And the corresponding threat:
This vulnerability has been detected in Microsoft Word. Cybercriminals have developed an active exploit for this application in the form of Microsoft Word document. Once this document is opened, another file called doc.doc is loaded. It contains an embedded HTA script, detected by Dr.Web as PowerShell.DownLoader.72. This HTA script, written using Windows Script syntax, calls the command interpreter PowerShell. PowerShell processes another malicious script that downloads an executable file to the attacked computer.
Currently, cybercriminals use this mechanism to install Trojan.DownLoader24.49614 on the computers of their victims. This Trojan downloads and runs other malicious software on infected machines.
Do you want to check whether PowerShell can be executed in your system? Click on Start → Run → powershell.

Because cybercriminals are using JScript and PowerShell, Dr.Web’s protection needed to be enhanced further. As a result, the Dr.Web Amsi-client protection module was developed. Its task is to check running scripts—PowerShell, JavaScript and VBScript.
This feature, available in Dr.Web Anti-virus for Windows and Dr.Web Security Space, operates on computers running Windows 10 (x 86, x 64) and Windows Server 2016. Dr.Web Office Amsi can be managed from the SpIDer Guard configuration tab.
#JavaScript #ScriptHeuristic #Dr.Web_technologies #vulnerability #Windows #terminology #cybercrimeThe Anti-virus Times recommends
Updates are not made for anti-virus products just so users can be reminded of them for the umpteenth time. Behind each update message you get are serious fixes and improvements. If the anti-virus needs rebooting, it probably means your protection needs to be enhanced to deal with emerging, new threats. Do not ignore these requirements—it is better to spend a few minutes for a reboot than to have to deal with the consequences of a sudden infection.




![Shared 2 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
15:10:14 2018-07-24
Неуёмный Обыватель
03:04:24 2018-07-21