Fishing for bots
Monday, June 4, 2018
Only law enforcement agencies are authorised to conduct the activities that must be undertaken to identify criminals. For example, they may be entitled by law to retrieve information from a computer belonging to an alleged perpetrator, an activity that is otherwise illegal in most countries. How then do anti-virus companies acquire information about how many devices are infected with a particular Trojan and in what countries the users of those devices are located?
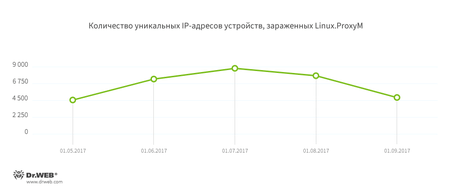
The diagram below shows the number of unique IP addresses belonging to infected devices. It should be noted that the graph only indicates how many bots are being monitored by Doctor Web's analysts, while the actual number of compromised devices may be higher.
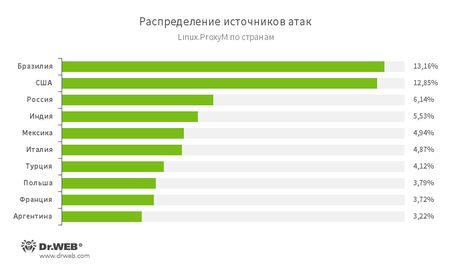
The below illustration shows the geographical locations from which
Conspiracy theorists will hardly be surprised—after all, they already know who actually makes malware!
But in reality, things are much more interesting. For starters, let's say a few words about how a botnet operates. Cybercriminals need their zombie networks to be resilient. And that's quite logical: if all bots communicate with a single C&C (command and control) server, the latter can be blocked easily (that's exactly what happened during the WannaCry outbreak). Naturally, in cases like this, the threat actors lose control of their network.
Another option is to use a special domain-generation algorithm (DGA) so that if a C&C server stops responding at a certain address, the bots will switch to another one. The attackers just need to promptly register the new domain names. But this approach is not failure-proof either. Security researchers may discern how the botnet operates, get in touch with the hosting provider and seize control of the server.
Another alternative is a peer-to-peer botnet where bots communicate with each other and exchange information. They don't send queries directly to servers which complicates their discovery and neutralisation.
Interestingly, with this network topology, computers with no access to the Internet can be enrolled in a botnet too. One PC with Internet connectivity is enough—all the other hosts on the network will get infected automatically.
Actually, sinkholing is the technology used to seize control over botnets. Botnet control is intercepted in several stages. First, anti-virus analysts examine the malicious code. Then they register a domain name the bots are expected to use in order to reach their C&C server. Then the security specialists wait until the bots start using the domain to connect to the server (or multiple servers). Generally speaking, it's just like fishing.
Researchers with the network security firm Damballa investigated a recently discovered botnet whose nodes use a DGA to connect to new C&C servers. The research team registered several domain names and managed to redirect the flow of data to their sinkhole at Georgia Tech Information Security Center (GTISC). The investigation continued for several weeks.
Sinkholing violates no laws. Furthermore, the technique not only helps researchers obtain information about botnets, but also is used to disrupt their operation by transferring control to a server maintained by the researchers, and frequently law enforcement agencies or a hosting provider assist them in their investigation. And, naturally, all investigation results are brought to the attention of the police.
Security researchers with Abuse.ch, BrillantIT and Proofpoint collaborated to sinkhole the EITest botnet, consisting of over 52,000 compromised servers.
Attackers used EITest to direct users to exploit kit (EK) landing pages, social engineering schemes, and more.
EITest emerged on the underground market in 2011 and was originally used by its bot herders only to further their own ends: to redirect traffic to sites hosting the Glazunov exploit, which was used to infect devices with Zaccess malware. At that time EITest was not particularly threatening, but in 2013 its botmasters began reorganising the structure of the network, and a year later they started to trade their botnet traffic with other criminals.
This was primarily done by selling hijacked traffic from hacked sites for $20 per 1,000 users and selling traffic blocks of a minimum size of 50,000 users, according to a Proofpoint researcher known as Kaffeine.
Earlier this year, information security specialists at BrillantIT managed to determine how compromised sites communicated with the C&C infrastructure. They seized the domain stat-dns.com, which allowed them to gain operational control over the entire EITest botnet. They also discovered that the botnet was directing the data flow from over 52,000 infected sites, most of which were using WordPress.
According to the researchers, the EITest botmasters never tried to restore control over their network so it is quite possible that they are now busy herding infected nodes into another botnet. Currently, traffic from several infrastructures, such as Fobos, Ngay and Seamless, is on sale on the underground market. Two other players—Afraidgate and pseudoDarkleech—haven't shown any signs of activity in recent months.
Botnets analysed and C&C servers hijacked. Congratulations!
Sinkholing has its limitations though: if a botnet uses multiple C&C servers, researchers may fail to seize them all. Therefore, they won't be able to control all the bots. Thus, they won’t know how big the botnet actually is since they will only know about the bots they control.
And it sometimes turns out that several teams of experts are examining the same botnet:
Microsoft, the FBI, and a number of financial institutions and IT companies presented the results of their joint operation to take down Citadel botnets. The report concluded that 1,000 botnet infrastructures were hijacked and as many as 4,000 domain names were seized.
But it turned out that some of the domain names belonged to other botnet researchers. One of the most recognised sinkholing experts was affected by the takedown. On June 7, the Swiss analyst running the site Abuse.ch lost over 300 domains. It's worth mentioning that security experts have suffered that kind of collateral damage before. Previously another researcher lost several hundred domain names when ZeuS infrastructures were shut down.
http://wwhois.ru/news-kompaniya-microsoft-po-oshibke-zahvatila-bolee-1000-chujih-domenov.html
Researchers can also use specific features of a decentralised system to gain control over all its nodes. Because attackers want their networks to be able to resist attempts to bring them down, they must be able to update the bots and send instructions to them. Therefore, all bots can be instructed to connect to a specific host or even uninstall themselves.
#botnet #terminologyThe Anti-virus Times recommends
Every action causes a reaction, and a countermeasure can be found for any trick.


![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
02:02:49 2018-07-30
vasvet
16:59:01 2018-06-16