You are much better off doing it yourself!
Friday, July 6, 2018
In our Ant-virus Times issues, we often talk about the need for users to adjust the settings of their applications to match their preferences. But what if a user doesn't have enough time or knowledge to do that? Is there a way to get an application configured and ready to be used right away?
The application Docker can help users accomplish this task. Docker performs containerisation—a technique allowing multiple isolated user-space instances (containers) to be used in order to run applications. With containerisation, programs are run in isolated containers with their specific settings and libraries. Unlike virtual machines, containers only contain data related to a specific application. The applications run on a computer's operating system but remain isolated from other applications.
Sound good? Apparently, yes. Docker images containing preconfigured applications started appearing on the Internet. But who can guarantee that, along with useful files, nothing unwanted has been placed in a container?
In summer 2017, unidentified hackers used their account docker12321 at Docker Hub to upload three images containing hidden code that facilitated crypto mining.
In the following months as many as 14 malicious images were uploaded under the same account.
The images scored 5 million downloads before they were deleted.
Five million downloads, and nobody cared to check the container's contents!
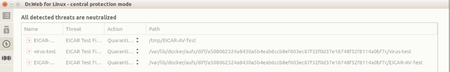
But, could it be that containers can't be scanned by an anti-virus? Let's add the EICAR test file to a container and launch our anti-virus scanner.
So it appears that none of the five million users had an anti-virus on their computers?
We'd also like to note that virtual machines may also have malware embedded in them.
A rogue crypto miner utilising GPU resources gets installed on computers along with Andy Android Emulator, which is available for Windows as well as macOS.
The user made several attempts to get in touch with Andy’s developers on Facebook but was repeatedly removed from the corresponding public group.
An analysis showed that the file GoogleUpdate.exe (GoogleUpdate.exe /svc) is run during the program’s installation. In turn, the file launches UpdaterSetup.exe which installs Updater.exe and makes sure it starts automatically whenever a user logs in to Windows. The description for GoogleUpdate.exe indicates that it is an "AndyOS Update", but the security researcher didn't understand why the file was named GoogleUpdate. Furthermore, GoogleUpdate.exe appears to be signed by Andy OS Inc, which indicates that it belongs to Andy OS Inc or that it has at least been signed by the company.
No commentary required…
#mining #malwareThe Anti-virus Times recommends
Believing that unknown strangers want to help everyone can have dire consequences. Scan all of your Internet downloads with an anti-virus.


![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
15:57:45 2018-07-09
vasvet
05:08:38 2018-07-09
razgen
01:20:46 2018-07-07