Judge by deeds or intentions?
Thursday, March 21, 2019
In early February, news of another fake anti-virus spread all over the World Wide Web. Done in JavaScript code, it worked in browsers and acted as if it was scanning user computers. In fact, this was hardly anything new.
The Anti-virus Times has spoken at length about Scareware on more than one occasion.
Fake anti-viruses are programs that imitate anti-viruses on the computers of gullible victims. They notify users about purported issues and try to sell them a full version that will solve all of their problems.
Let's take another look at how they work.
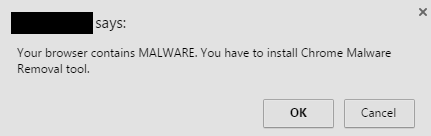
When a user visits a certain site, they see a dialogue box that imitates the anti-virus scanning process and then displays a report about the threats that were detected.
Victims are advised to use the "anti-virus" to resolve this problem. Once installed, the program gets added to the list of user startup applications — Login Items. Therefore, it is activated every time the user logs on or the computer is turned on and regularly "finds" malware in the system and reminds the victim of the need to "cure" it.
You can find a screenshot of a typical fake anti-virus dialogue box in this issue:
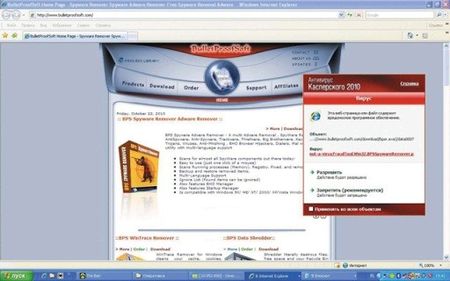
Another good example:
If a message appears from a popular anti-virus, what should the user think?
Fraud schemes of this kind (just like many others) become feasible because users aren't vigilant enough and often lack a sufficient IT background—no computer can be scanned via a browser window unless an anti-virus is actually installed on it. However, people fall for the trick, and to a startling degree. It’s completely scary! According to statistics, in now-distant 2010 as many as 150 million copies of scareware were downloaded across the Internet.
Tens of thousands of users fell victim to the fraud.
And that's not the biggest number. Here is a quotation from another decade-old news post.
In the first two weeks of October, Doctor Web was registering 2.5 million scareware detections on a daily basis.
Over 2.5 million in 24 hours! Those were applications rather than browser windows, but still. Under the Dr.Web classification system, these malware samples belong to the Trojan.Fakealert family. New species of the same breed emerge literally every day. For example, on February 11, 2019, Trojan.Fakealert.45800 was added to the Dr.Web database. That is species number 45,800! This is by no means the biggest family, but the figure is still impressive.
Time goes by, but users (sometimes even experienced ones) still trust fake anti-viruses. Knowing full well that their anti-virus can’t always recognize malicious programs, they may assume that their computer has indeed been infected and that the anti-virus just doesn't know about it:
In one incident, a dissatisfied user complained that a legitimate anti-virus was blocking the scareware. "That's my anti-virus! I paid for it!", he said.
Most fake anti-viruses scare users into giving money to scammers. But they can also sometimes help attackers do much more than that.
If I were a cybercriminal with substantial financial resources at my disposal, I would recruit a team of talented professionals to create a good free anti-virus. The anti-virus would scan the entire system, encrypt the most important user documents, and upload them to my server.
Fake anti-viruses can also be used to create a smokescreen for other malware.
Once the malware has infected a system, it notifies users that they are using illegal copies of anti-virus software, which can harm their PCs. Then users are prompted to remove the anti-virus, and the security software will be removed regardless of which option they choose.
The malware can discover and uninstall security software from Microsoft, AVG, PC Tools, Zone Labs and many others.
Once the system is rid of legitimate anti-virus software, the rogue application starts installing AnVi Antivirus, which is in fact not an anti-virus at all. The program immediately detects malicious files and offers users the option to have their systems cleaned for a fee.
And then it can install another Trojan in the guise of a fake anti-virus and steal data or mine cryptocurrencies.
And if a malware outbreak erupts, it can also offer a cure! One Trojan.Fakealert species is spread in the guise of a utility that ostensibly cures local networks of Conficker (Win32.HLLW.Shadow.based).
The Anti-virus Times recommends
- Don't trust anti-virus applications whose names you don't recognise! No legitimate anti-virus will scan a system without your consent. Online scanning services do exist, but users must initiate the procedure themselves.
- Even though Dr.Web recognises and neutralises scareware, users can still fall victim to a scam. After all, scareware on a website is just a piece of code that in fact does nothing and inflicts no system damage whatsoever!
- SpIDer Gate uses a database of bogus sites to block access to fraudulent webpages. Just like the Parental Control databases, this database is available in Dr.Web Security Space. However, this feature is not present in Dr.Web Anti-virus. Because of that, we recommend opting for Dr.Web Security Space.
- With anti-viruses like those, there is no need for malware. Scareware is not only about luring users into paying a relatively small sum of money. It is also about enabling attackers to pursue their malicious agenda without fear of being detected by legitimate anti-viruses. Therefore, do not install dubious applications promising you reliable protection.


![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
razgen
22:17:51 2019-03-21
Неуёмный Обыватель
08:09:23 2019-03-21