Open windows
Wednesday, August 17, 2016
Today, we’re surrounded by computers at work, as well as at home. If an urgent task requires our attention at home, we don’t even need to get off the couch and go to the next room. Using a remote connection is much more convenient. A Windows computer (as well as machines running other OSs) can be accessed remotely via the RDP protocol (MS Windows includes the Remote Desktop Connection component). You can also opt to use another program. Quite a few alternatives exist, such as Radmin and TeamViewer.
However, remote access that is protected by a weak password (and has unclosed vulnerabilities) is a perfect gift for criminals.
"When I sat down at my computer, I saw my mouse moving across the screen. Of course, I immediately revoked remote control, and asked who was there" — a Reddit user wrote. — "At that point, he disconnected and attempted to connect to my Ubuntu server, which has all my backups. Good thing I anticipated what he was going to do and connected to my server as soon as he disconnected from my computer. I revoked his permission before he tried to open Firefox. Immediately afterwards, I started panicking; I thought he’d just stolen all my passwords".
Genuine panic spread among TeamViewer users overnight, from June 1-2. The company's official site and servers were unavailable for several hours; meanwhile numerous messages about a hacker attack and stolen money were popping up on Reddit and in social media. TeamViewer spokespeople gave assurances that no attack had occurred and that their servers were unavailable due to some DNS issues.
Simply installing a remote administration program may be enough to let attackers into a system.
A TeamViewer installer containing a backdoor was discovered on the Internet. It should be noted that this distribution included TeamViewer 6.0.17222.0, released back in December 2010.
Criminals make extensive use of remote administration software too.
Information security experts know about several malware species that use TeamViewer to access a target machine without user consent.
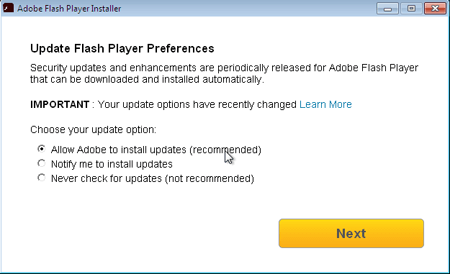
For example, Trojan.MulDrop6.39120 is disguised as an Adobe Flash Player update. It not only installs the flash player onto a Windows machine, but also secretly saves to the disk: the TeamViewer application, the BackDoor.TeamViewer.49, and the Trojan’s configuration file. An actual Flash Player installer window is displayed during installation.
Usually, malicious programs use TeamViewer to facilitate unauthorised access to the infected machine. However, BackDoor.TeamViewer.49 needs TeamViewer for a different reason: it makes heavy use of the routines incorporated into the program's process. In addition, when launched, TeamViewer automatically loads the file avicap32.dll into the memory, something criminals have taken advantage of: they’ve placed a malicious library with the same name into the directory into which Trojan.MulDrop6.39120 saves the application. So when TeamViewer starts, the file is automatically loaded into memory. Once TeamViewer is launched, BackDoor.TeamViewer.49 removes its icon from the system tray and disables error reporting.
The Anti-virus Times recommends
- Do not install programs from unknown sources—such programs are most likely infected, pirated copies. Always download software programs from the official sites of their respective developers (the right holders).
- Installing pirated versions of important software is fraught with danger. Pirate benefactors died out long ago, and a cracked version is very likely to contain a Trojan.
- Work under an account that doesn't have permissions to install software. Ordinarily these permissions are rarely needed, and their absence will make things much more difficult for malware.
- Regularly check the list of installed programs and the autorun list. In Windows go to Start→ Control Panel → Programs and Features, and view the list of installed programs. If you come across programs that you have never run or installed, look for information about them online—it may turn out that you don’t need them.
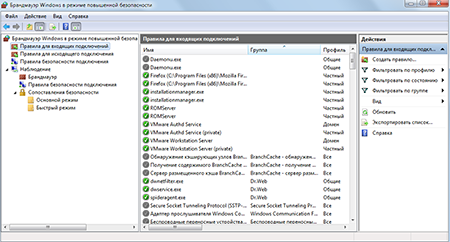
- Do not leave ports open if they aren't in use. You can use the firewall that comes with Dr.Web Security Space to establish rules for the applications you use and view the list of the ports they listen to.
To configure the Windows Firewall, go to Start → Control Panel → Windows Firewall.
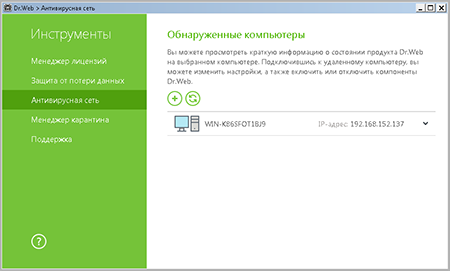
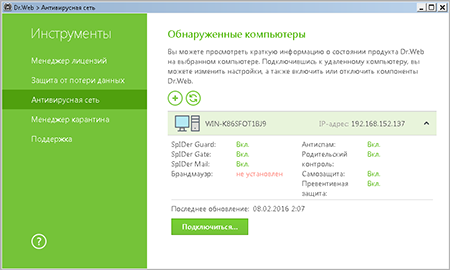
- If you do not require full access and only want to control your anti-virus security, you can use the Anti-virus Network component of Dr.Web Security Space.
To launch it, in the agent menu select Tools → Anti-virus network.
The item Anti-virus network is only available in the Administrative mode.
To access a remote anti-virus, select the computer on the list, and press Connect.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
02:00:43 2018-08-20
vasvet
19:20:24 2018-07-02